
The Lapsus$ data extortion group has released what they claim to be data stolen from the Nvidia GPU designer. The cache is an archive that is almost 20GB large.
While the U.S. chipmaker giant has yet to confirm a breach on its network, the threat actor has been active with messages about the alleged hack since February 24.
Nvidia silent to extortionist's claims and leak
Replying to a request for comments from BleepingComputer on Friday about an incident that reportedly took down some of its systems for two days, Nvidia said that it was investigating what looked like a cyberattack.
In a reply to BleepingComputer, a company spokesperson said that Nvidia will issue an updated statement on Sunday but it never came. Several subsequent requests from us remained unanswered.
Reporting on the outage and what caused it, The Telegraph cited an insider saying that the intrusion “completely compromised” the company’s internal systems.
Lapsus$ said that they stole 1TB of data from Nvidia and that they were prepared to publish it unless the company paid a ransom demand.
The first round of messages from Lapsus$ included a leak of what the actor said were hashed passwords of all Nvidia employees and a claim that the company hacked back to encrypt their virtual machine with the data.
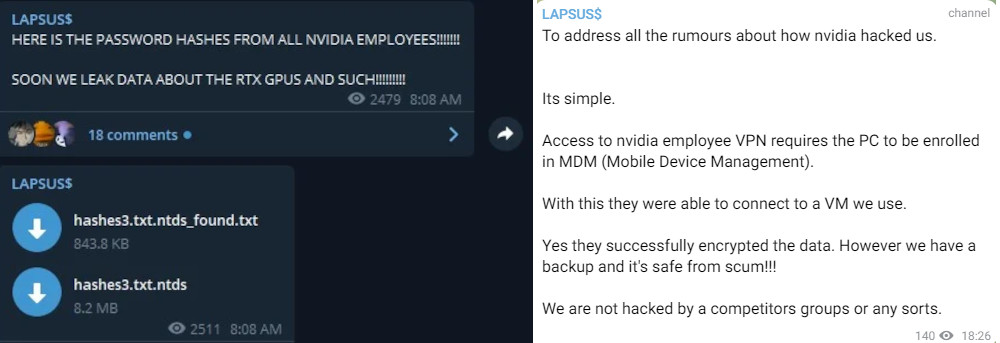
In an odd move, the extortion group removed all messages related to the Nvidia and resumed the stream of communication today with a note reiterating that they “hacked Nvidia.”
In multiple messages today, Lapsus$ provided more details about their incursion. “We were into nvidia systems for about a week, we fastly escalated to admin of a lot of systems,” the actor said.
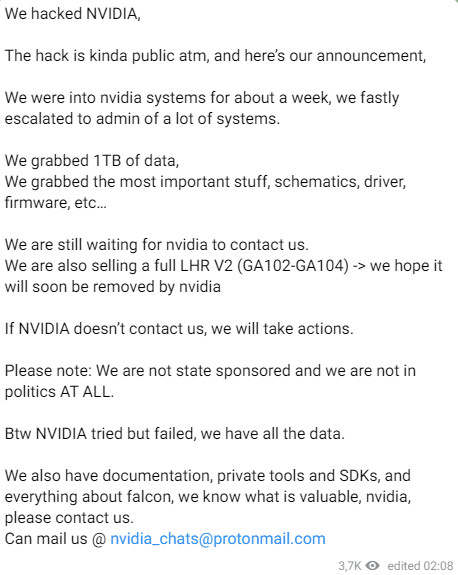
They said they stole important files during the breach that include “stuff, schematics, driver, firmware,” and that they are willing to sell some of it:
“We are still waiting for nvidia to contact us. We are also selling a full LHR V2 (GA102-GA104) -> we hope it will soon be removed by nvidia” - Lapsus$
LHR is Nvidia’s lite hash rate technology that enables graphics cards to reduce a GPU’s mining capacity. The Lapsus$ extortion group hopes that Nvidia will remove this limitation.
For this reason, they’re asking the GPU maker to remove the LHR limitations in the GeForce RTX 30 Series firmware, threatening to leak the folder with the hardware specifications.
.jpg)
The actor also claims to have documentation, company private tools, SDKs, “and everything about falcon” - Nvidia’s proprietary control processor.
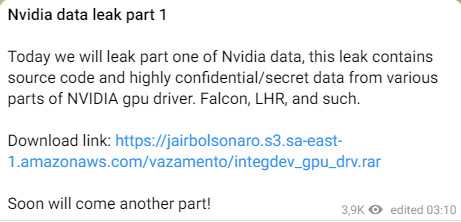
The next message was a link to “part one of Nvidia data,” hosted on Amazon infrastructure, containing “source code and highly confidential/secret data from various parts of NVIDIA gpu driver. Falcon, LHR, and such.”
According to the threat actor, Nvidia filed an abuse report to stop the sharing. However, Lapsus$ switched to leaking the info over torrent and said that they would not re-upload the file.
The size of today’s data leak that Lapsus$ claims to have stolen from Nvidia is around 20GB and consists of an archive named “integdev_gpu_drv.rar.”
The actor says that the archive includes important source code and that they have enough information for a good developer to be able to create a bypass for Nvidia's LHR.
They also added that they're selling a LHR bypass that would disable the technology “without flashing anything.” This would enable a cryptocurrency mining operation to make the most of Nvidia graphic cards.
For now, Nvidia is keeping quiet about Lapsus$ claims and the data they shared. It is unclear how damaging this leak is to Nvidia or what secrets it may contain but there is a good chance for sensitive data to be present in a document archive of about 20GB.
Shortly before publishing this article, Nvidia responded with the following statement to BleepingComputer's request:
“We are investigating an incident. Our business and commercial activities continue uninterrupted. We are still working to evaluate the nature and scope of the event and don't have any additional information to share at this time."



Comments
Hevihitr - 2 years ago
Nvidia should lock out minetards so they can fk off and find another way to make their fake money and stop upping prices of GPU's so people who want to use the for their intended use can without having to sell a body part to buy one, #fkminetards